Table of Contents
Introduction
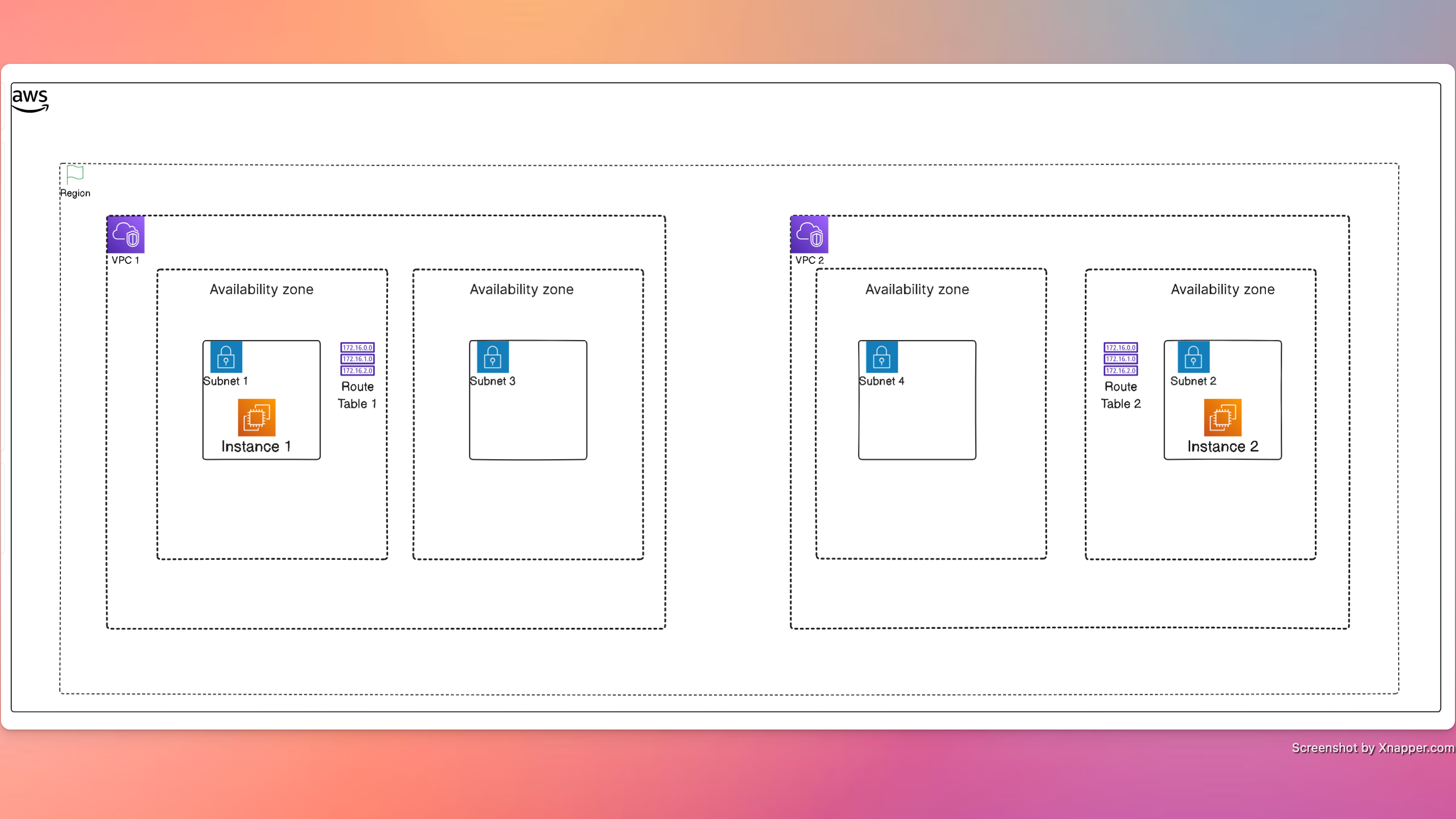
We need to enable communication between two instances in separate VPCs. Here is the existing architecture
-
Two VPCs each with isolated subnets in two AZs and associated route tables.
-
In each VPC exists one EC2 instance.
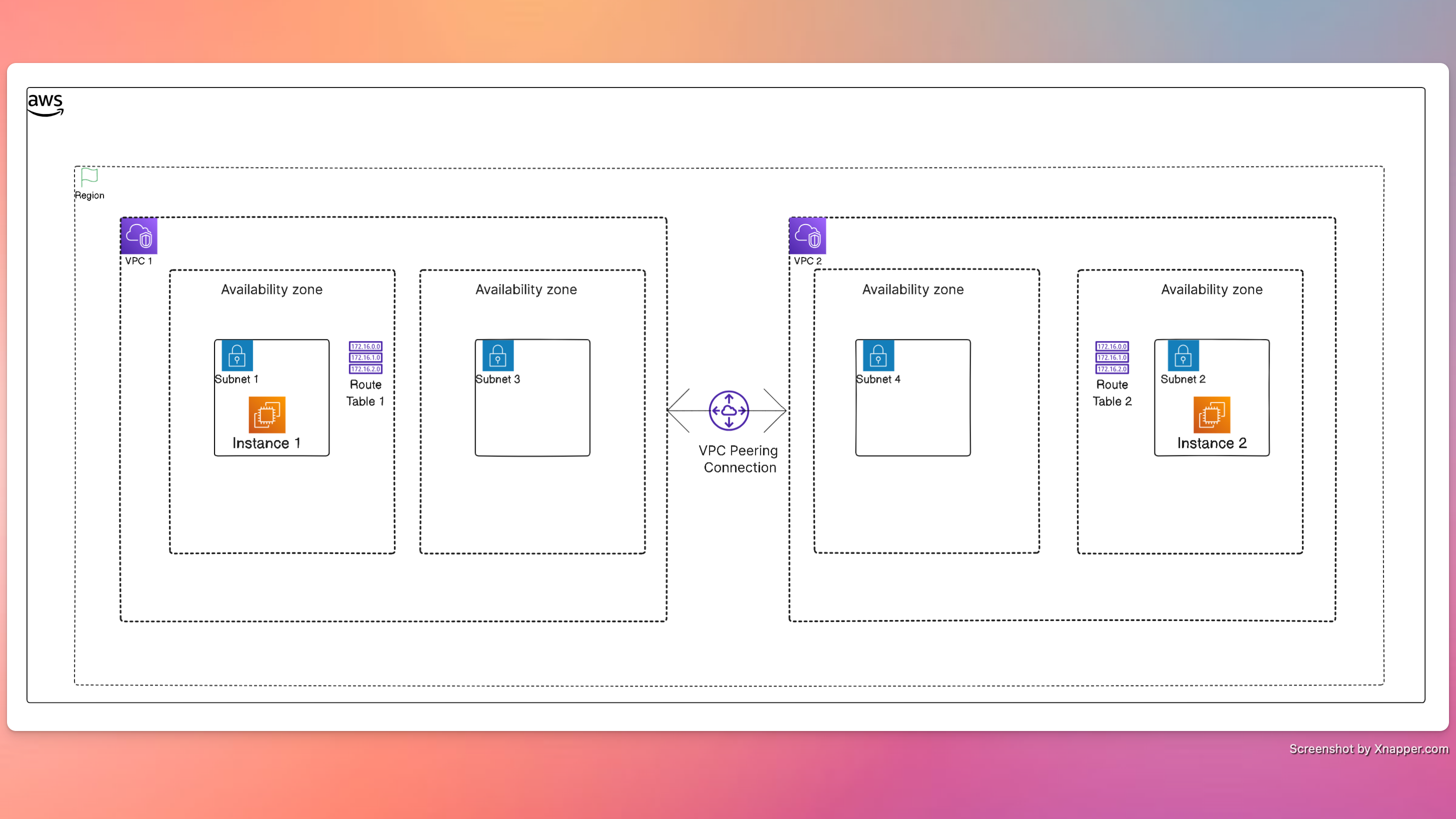
Design
We need to request a peering connection between two VPCs, accept the peering connection, update the route table for each vac subnet.
Steps
- Create a VPC Peering connection to connect VPC1 and VPC2.
VPC_PEERING_CONNECTION_ID=$(aws ec2 create-vpc-peering-connection \
--vpc-id $VPC_ID_1 --peer-vpc-id $VPC_ID_2 --output text \
--query VpcPeeringConnection.VpcPeeringConnectionId)
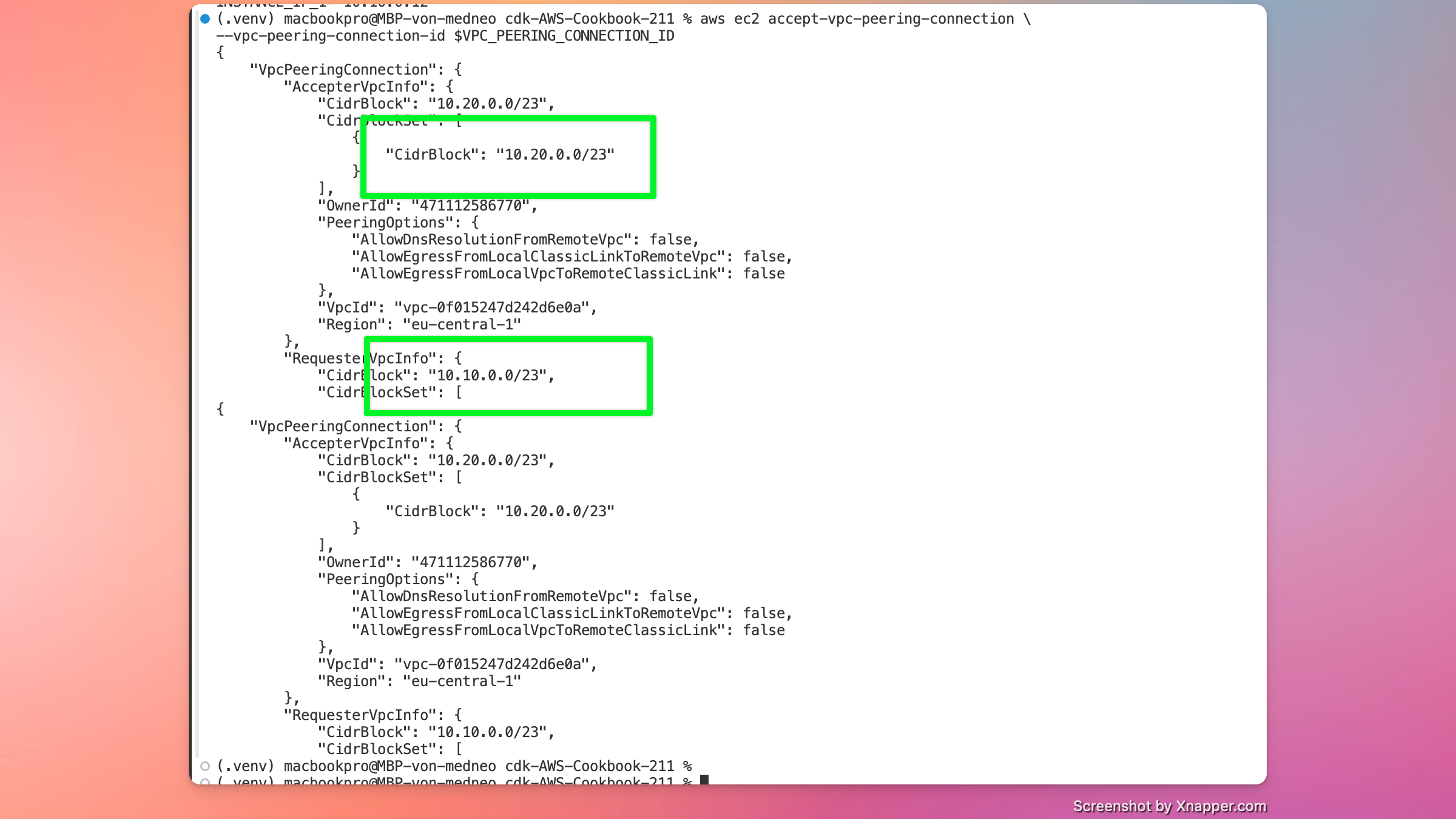
- Accept the peering connection
aws ec2 accept-vpc-peering-connection \
--vpc-peering-connection-id $VPC_PEERING_CONNECTION_ID
- Add a route in each subnet to direct traffic destined for the peered Net to the VPC_PEERING_CONNECTION_ID
aws ec2 create-route --route-table-id $VPC_SUBNET_RT_ID_1 \
--destination-cidr-block $VPC_CIDR_2 \
--vpc-peering-connection-id $VPC_PEERING_CONNECTION_ID
aws ec2 create-route --route-table-id $VPC_SUBNET_RT_ID_2 \
--destination-cidr-block $VPC_CIDR_1 \
--vpc-peering-connection-id $VPC_PEERING_CONNECTION_ID
- Add an Ingress rule to instance 2’s security group to allow ping from instance 1.
aws ec2 authorize-security-group-ingress \
--protocol icmp --port -1 \
--source-group $INSTANCE_SG_1 \
--group-id $INSTANCE_SG_2
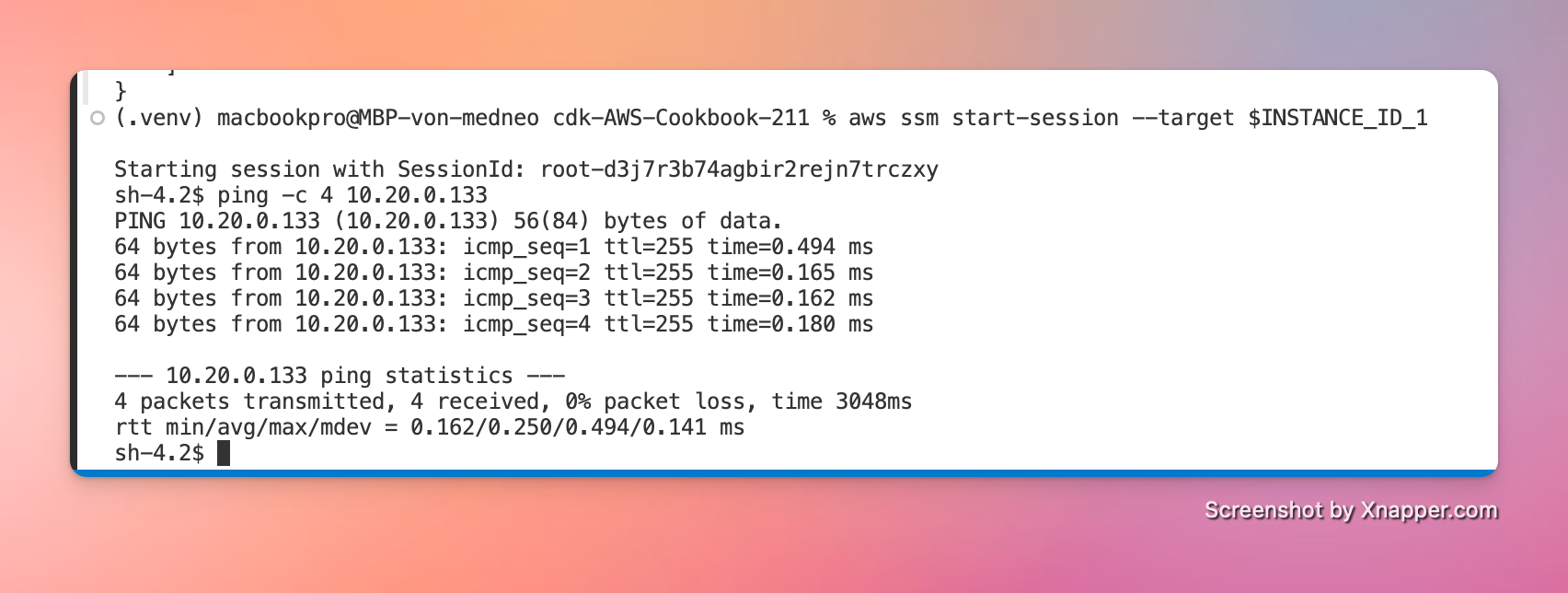
Validation Checks
We connect to the EC2 instance by using SSM Session Manager:
aws ssm start-session --target $INSTANCE_ID_1