How to Implement and Manage LAPS for Microsoft Entra ID and Intune
Implement and manage LAPS for Microsoft Entra ID
When LAPS (Local Administrator Password Solution) is not implemented, administrators often resort to two insecure practices for managing local administrator access on computers:
-
Shared Local Admin Password: In this scenario, administrators set a single, uniform local administrator password across multiple computers. This practice poses a significant security risk because it lacks granularity and accountability. The reasons for its insecurity are as follows:
-
Uniformity: Using a single shared password for all computers means that if it’s compromised on one system, it’s compromised on all, exposing the entire network to potential breaches.
-
Limited Accountability: When multiple administrators have access to the same password, it becomes challenging to trace who performed specific actions or changes on a given computer, hindering accountability.
-
Difficulty in Rotation: Regular password rotation, a crucial security practice, becomes cumbersome when managing shared passwords across numerous systems. Stale passwords increase vulnerability.
-
-
Using Normal Credentials as Local Admin: Some administrators may choose to log in as local administrators on remote systems using their standard domain credentials. While this approach may seem convenient, it introduces security risks, particularly regarding LSASS credential theft:
-
Credential Exposure: When administrators use their domain credentials on remote systems, these credentials are sent across the network and stored temporarily in LSASS memory. This exposure creates an opportunity for attackers to capture and exploit these credentials.
-
LSASS Vulnerability: The Local Security Authority Subsystem Service (LSASS) stores credentials in memory during the authentication process. Malicious actors can employ techniques like Pass-the-Hash (PtH) attacks to steal these stored credentials, compromising administrator accounts and potentially gaining unauthorized access.
-
In both cases, the absence of LAPS and secure local administrator management practices increases the organization’s susceptibility to security breaches and unauthorized access. Implementing LAPS helps mitigate these risks by automating the management of unique, regularly rotated local administrator passwords, enhancing security and accountability across the network.
Password management for administrator accounts on AD DS or Azure AD–joined computers is a significant problem for Windows administrators. Implementing Local Administrator Password Solution (LAPS) is one solution.
LAPS enables you to secure and help protect your Windows devices’ local admin passwords. Features include the ability to back up passwords and auto-rotate passwords. You must configure two related settings to enable and use LAPS in your Azure AD tenant:
• Enable LAPS in Microsoft Entra • Configure LAPS using Intune
Enabling LAPS in Microsoft Entra
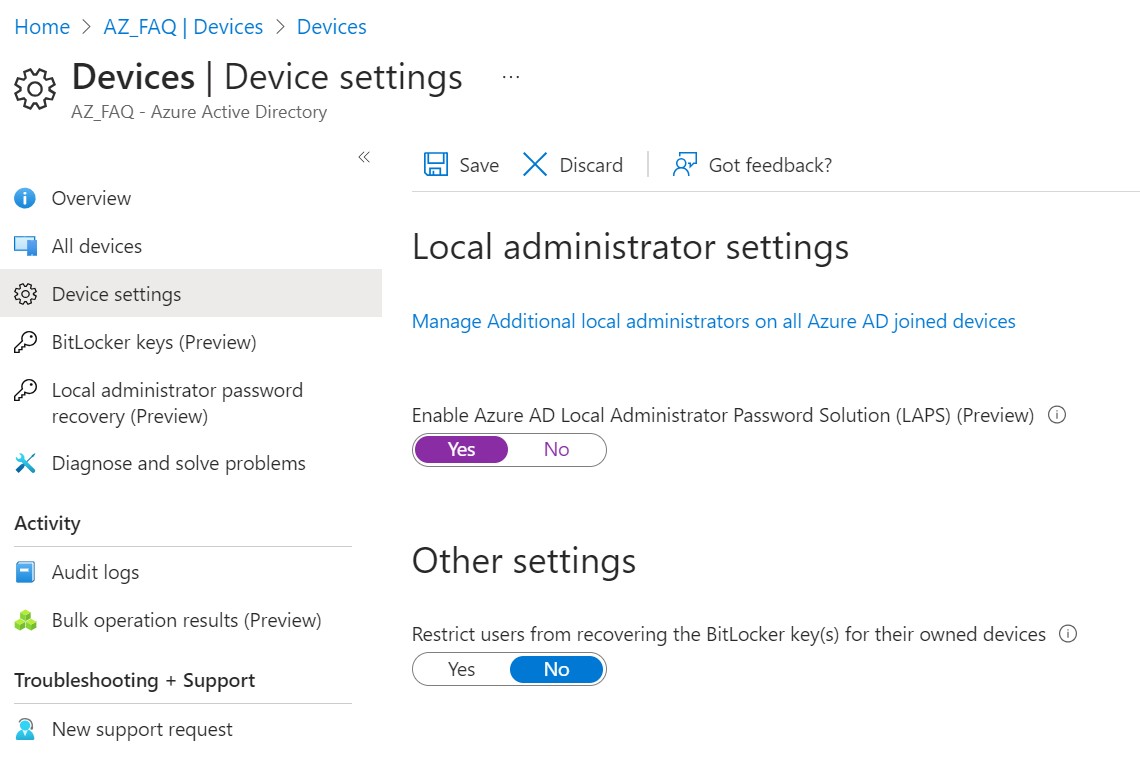
Before you can implement LAPS, you must enable it within your Azure AD tenant. You do this using the Microsoft Entra admin center. Use the following procedure:
- Open Microsoft Entra admin center.
- Expand Azure Active Directory in the navigation pane.
- Expand Devices and then select All devices.
- Click Device settings.
- Under the Local administrator settings, heading turn on the Enable Azure AD Local Administrator Password Solution (LAPS) setting.
I consistently seek to achieve configurations through Microsoft Graph API calls, even when UI options are available, offers automation, consistency, version control, scalability, security, and enhanced auditing capabilities.
In this case however Microsoft Document for LAPS setting is inadequate.
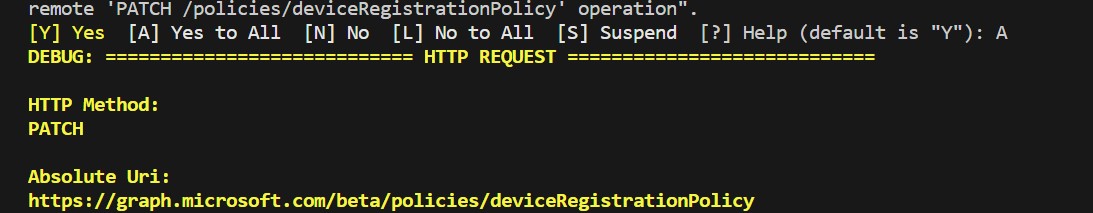
Commandlet Update-MgBetaPolicyDeviceRegistrationPolicy is not working as expected.
I tried running with the Debug Switch to realize it is sending the PATCH method however as per the documentation we will require PUT method and send all the properties.
# Import the JSON file as a PowerShell object
$bodyParams = Get-Content $jsonFilePath -Raw
$LocalAdminPwd = @{
"IsEnabled" = "true"
}
Update-MgBetaPolicyDeviceRegistrationPolicy -LocalAdminPassword $LocalAdminPwd -Debug
To address the issue, I took the following steps: I obtained the list of settings for the Device Registration policy within Entra ID and then made the required modifications to activate the LAPS policy setting.
#Get the Setting from URI and Store In a File
Get-MgBetaPolicyDeviceRegistrationPolicy | ConvertTo-JSON | Out-File LAPSSettings.json
# Modify the JSON File and Update the Setting
$jsonFilePath = ".\LAPSSettings.json"
$json = Get-Content $jsonFilePath -Raw
$json = $json -replace '"IsEnabled": false', '"IsEnabled": true'
Connect-MgGraph -Scopes "Policy.ReadWrite.DeviceConfiguration"
Invoke-MgGraphRequest `
-Method PUT `
-Uri "https://graph.microsoft.com/beta/policies/deviceRegistrationPolicy" `
-Body $json `
-ContentType "application/json"
Configuring LAPS using Intune
To create an account protection policy in Intune, follow these steps:
- Launch the Microsoft Intune admin center.
- Navigate to Endpoint security in the sidebar and select Account protection.
- In the details pane, click on the “Create Policy” button.
- On the “Create a profile” page, choose “Windows 10 and later” from the Platform list.
- From the Profile list, select “Local admin password solution (LAPS).”
- Click the “Create” button.
- In the “Create profile” wizard, provide a name on the Basics tab, and then click “Next.”
- Configure your desired settings on the Configuration settings tab.
- Click “Next” and configure any scope tags if necessary.
- Proceed to the next step to assign the policy to the appropriate device group.
- Once you’ve made your assignments, click “Next” and then finalize the process by clicking “Create.”


Read Device Password
If Everything goes right, you will be able to retrieve the password by the following method.
To view the local administrator password in the Microsoft Entra admin center, follow these steps:
- Navigate to All devices and select the appropriate device.
-
On the **Device Properties** page, click the Local administrator password recovery tab. - Click the Show local administrator password link.
You can also review the password using the Microsoft Intune admin center:
- In Intune, select Devices in the navigation pane.
- Choose All devices and then select the appropriate device.
- Click the Local admin password tab in the navigation pane.
- Click the Show local administrator password link.
You can retrieve the password using the following Powershell Script.
Connect-MgGraph -Scopes "DeviceLocalCredential.Read.All"
Get-LapsAADPassword -DeviceIds "XXXXXX-8dcc-43bc-bef7-XXXXXXX" -IncludePasswords -AsPlainText
Conclusion
In this article, we have discussed how to implement and manage LAPS for Microsoft Entra ID. LAPS is a powerful tool that can help you secure your local administrator passwords and improve the security of your organization. By following the steps outlined in this article, you can easily get started with LAPS and start reaping the benefits of improved security. Implementing and managing the Local Administrator Password Solution (LAPS) for Microsoft Entra ID is crucial for enhancing security and accountability in your organization’s network. Without LAPS, administrators often resort to insecure practices like shared local admin passwords or using normal credentials as local admin, both of which pose significant security risks.
Shared local admin passwords lack granularity and accountability, making it challenging to trace actions and changes on specific devices. Additionally, rotating passwords becomes cumbersome, leading to security vulnerabilities due to stale passwords.
Using normal credentials as local admin introduces security risks, as credentials are exposed and stored in memory, potentially allowing attackers to capture and exploit them.
Here are some additional tips for implementing and managing LAPS:
- Make sure that all of your devices are joined in Azure AD and enrolled in Intune.
- Create an account protection policy in Intune for LAPS and assign it to all devices.
- Configure the LAPS policy settings to meet your organization’s needs.
- Regularly rotate the local administrator passwords.
- Test the LAPS solution to ensure that it is working properly.
